Main points: 1. The quantum threat is not distant, but is 'currently ongoing'
2. The impact of quantum attacks is not uniform; some subfields are at extremely high risk
3. Post-quantum signature systems are still immature, and reckless migration could be even more dangerous
4. Industry response strategy: advance steadily, transition in layers, non-panic migration
Content: Quantum computing will not destroy encryption systems in the short term, but 'collect first, decrypt later' (HNDL) poses risks for blockchain historical data, especially for privacy coins relying on ECC, facing the risk of being traced back to anonymity in the future. Current post-quantum signature technology is still immature, and reckless migration could be even more dangerous. The industry should take a robust approach: use hybrid encryption to resist HNDL in the short term, and plan for an upgradable signature system in the medium to long term. Privacy chains need to prioritize addressing future privacy exposure issues. This quantum threat is more like a catalyst for 'modernizing cryptography' rather than an impending disaster.
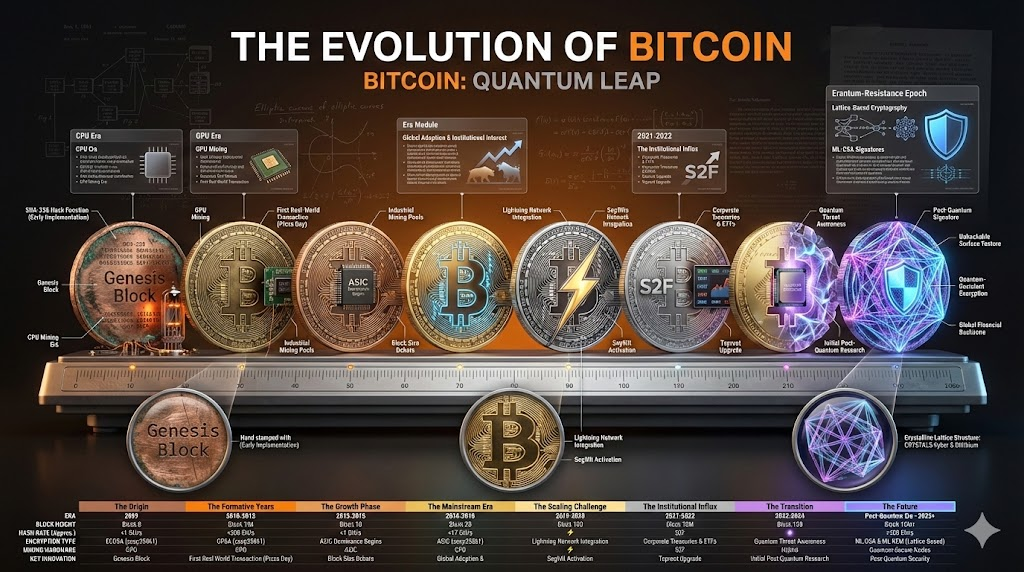
2025: How Cryptocurrencies Can Counter the Threat of Quantum Computing
—A Systematic Reconstruction of Asset Security from Underlying Cryptography
The rapid advancements in quantum computing have brought a crucial, long-neglected issue to the crypto industry in 2025:
When quantum computing has the ability to break mainstream cryptographic systems, will cryptocurrencies still be secure?
Over the past decade, “quantum attacks” have often been regarded as a long-term risk, but recent hardware advancements, improved stability of qubits, and a surge in investment in quantum research in various countries have gradually transformed it from a theoretical threat into a predictable technological milestone.
This means that, for the first time, the crypto industry must consider its quantum resistance, upgrade paths, asset migration costs, and the resilience of the financial system in a systems engineering manner.
This article will use the research report released by A16Z on Sunday as a framework to break down the difficulties, opportunities, and advice for practitioners in the crypto industry.
I. Can quantum computing really "kill Bitcoin"?
You may have seen comments like this on Twitter and Reddit.
"Quantum computing will kill Bitcoin/all public blockchains within 5 years..."
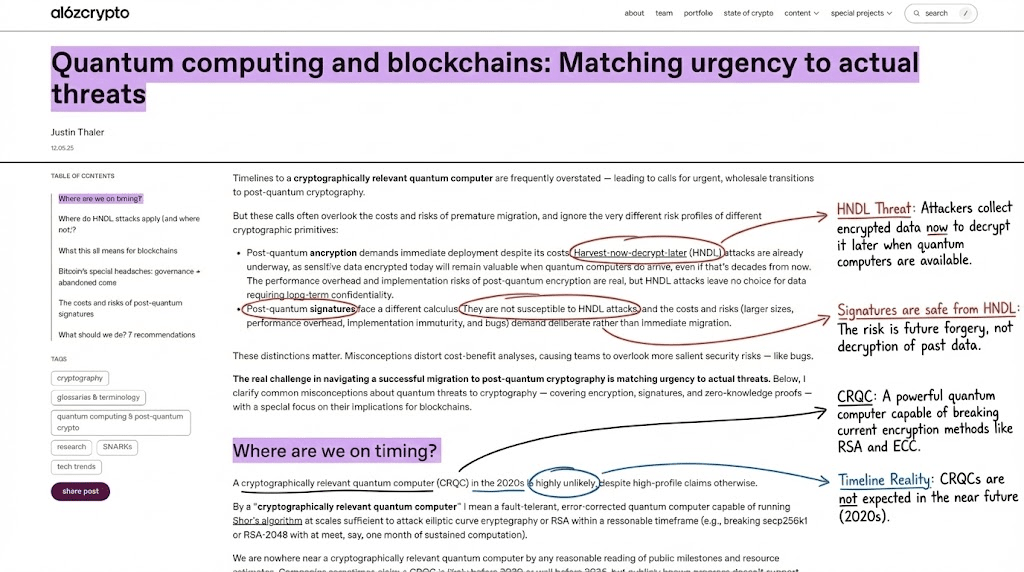
First and foremost, it is essential to understand that for encryption, quantum attacks are no longer a future threat, but rather a present-day threat model—the so-called Harvest-now-decrypt-later (HNDL).
For example, Russia's cyber intelligence agency intercepted a large number of internet communication data packets encrypted with TLS 1.2/1.3. Although it cannot crack them now, it may be possible to decrypt the sensitive content at that time after the development of quantum computers in the future.
For cryptocurrencies, the threat model of HNDL is equally real and imminent. This is because any encrypted data protected today using non-quantum-resistant algorithms can be archived indefinitely by attackers.
The TLS 1.2/1.3 encrypted internet communication data packets collected by Russian intelligence correspond to public keys, addresses, transaction data, and layers of zero-knowledge proof evidence chains that are currently unbreakable.
It is important to note that digital signatures, which are commonly used in blockchain systems, do not possess the characteristic of encryption that "storage and subsequent cracking do not affect past security."
In other words, the risks of quantum mechanics are real, but their severity has been exaggerated. What truly requires immediate action are certain subfields within cryptography, not the entire industry.
A16Z's research report argues that the emergence of a cryptographically significant quantum computer "remains an ambitious goal, even if it takes ten years."
II. Which sub-fields are most affected?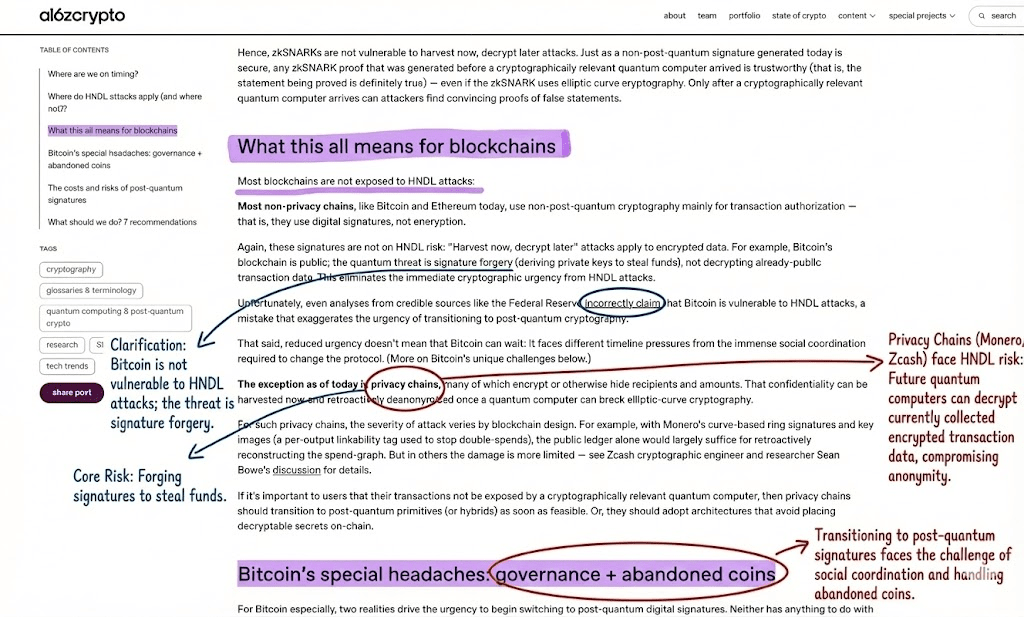
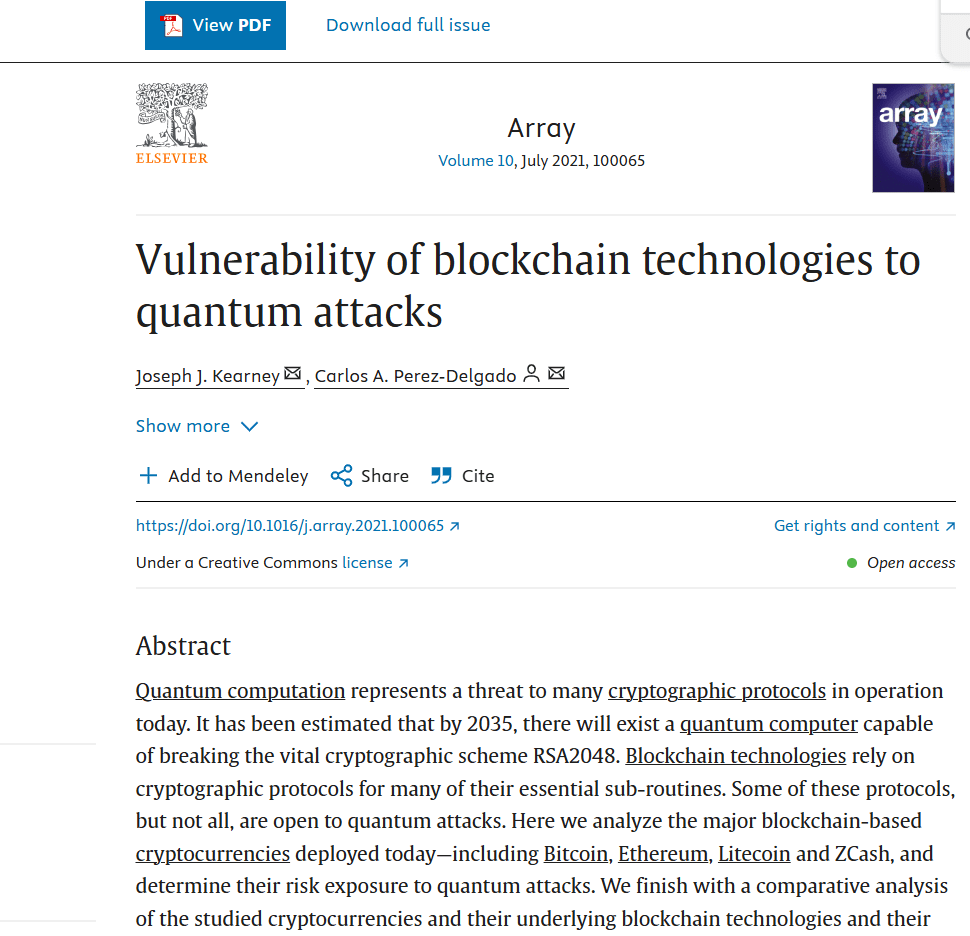
A 2021 academic paper titled "Vulnerability of blockchain technologies to quantum attacks" pointed out that systems including mainstream blockchains such as Zcash and Monero are highly vulnerable to quantum attacks if their underlying public key/signature mechanisms rely on ECC.
A recent article on privacy coins, Quantum Canary's report "Quantum Attacks and The Future of Privacy Coins," clearly points out that Monero and Zcash's current privacy mechanisms both rely on ECC. This means they are "highly likely to be retroactively deanonymized under future quantum computing conditions."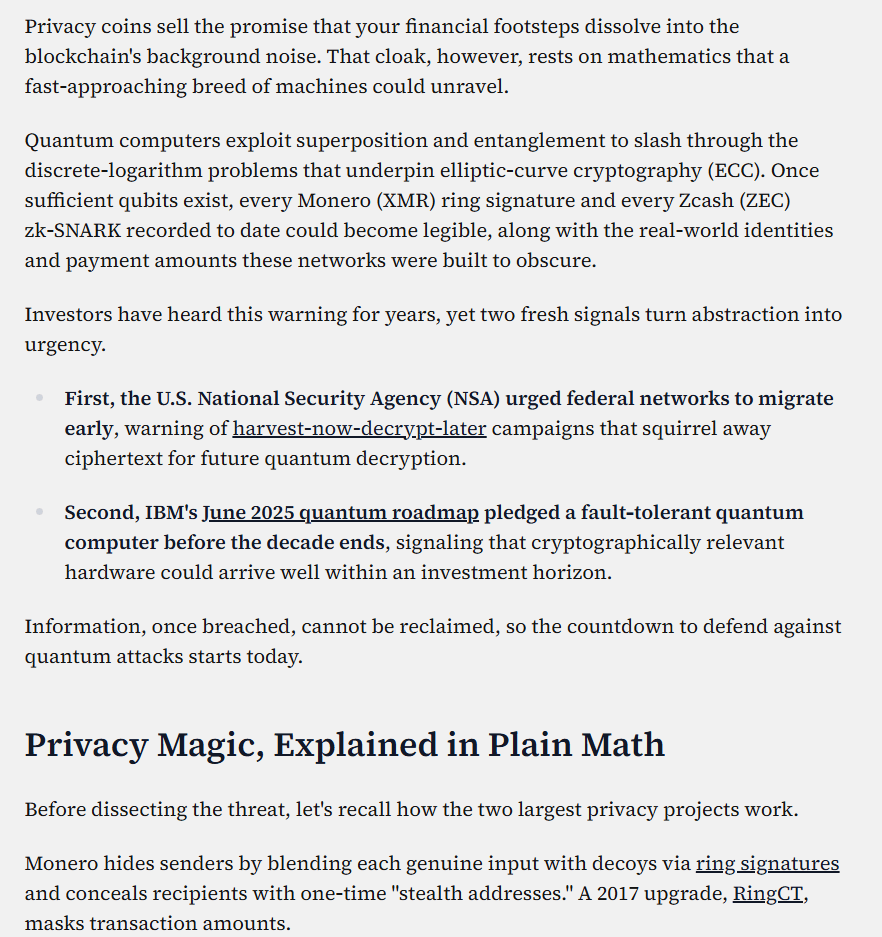
The report further points out that neither of them has yet deployed true post-quantum primitives in production environments, meaning that all historical transactions—until quantum computing matures in the future—are an “at-risk” privacy debt.
Public discussions about this risk have sparked controversy within the community and industry. For example, a recent security blog post about Bitfinex explicitly stated that when quantum computers become powerful enough to break ECC, privacy chains that rely on ECC, including Zcash, will face the real risk of "retroactive deanonymization" of past transaction privacy.
III. Costs and Risks of Post-Quantum Signature Technology
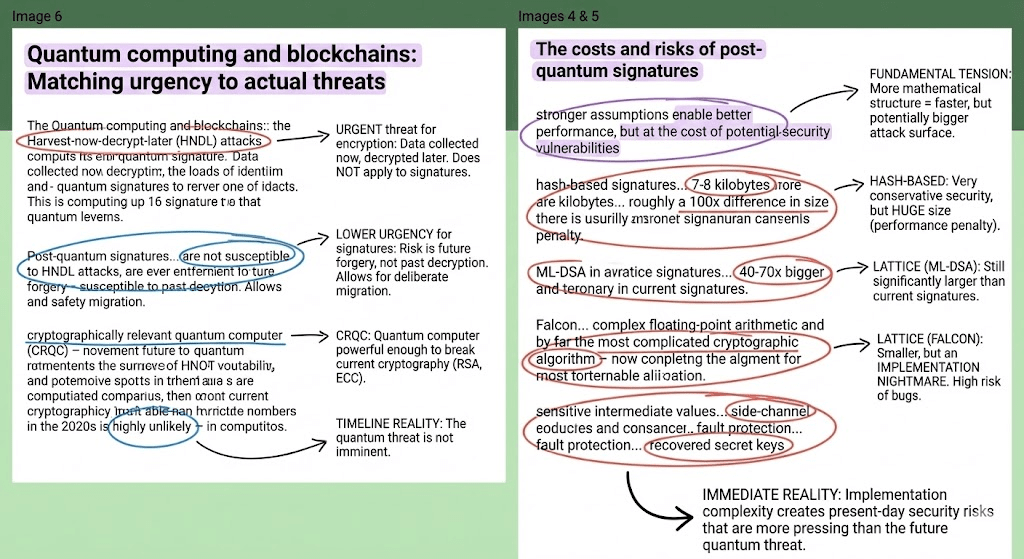
The reason why post-quantum signatures cannot be deployed hastily is that all current mainstream solutions—whether based on hashing, codes, lattices, message queues (MQ), or homology—are built on mathematical assumptions that are still under testing. The stronger the structure and the better the performance, the more attack surfaces are likely to be exposed, thus security has not truly been solidified. Meanwhile, while lattice-based solutions are closest to usability, their signatures are generally tens of times larger than ECDSA and are complex to implement, making them susceptible to side-channel and fault-based attacks, posing a risk more immediate than quantum mechanics itself. More importantly, blockchains heavily rely on efficient aggregate signatures (such as BLS), and mature post-quantum aggregate solutions have not yet emerged. A hasty migration would damage the performance and availability of the entire system. Historically, candidate solutions like Rainbow and SIKE have been directly breached by classical methods, proving that premature deployment can be counterproductive. Therefore, signature systems must be developed steadily, allowing the mathematical foundations, security implementations, and ecosystem toolchains to mature before migration, rather than being hastily switched driven by quantum mechanics panic.
IV. What should we do?
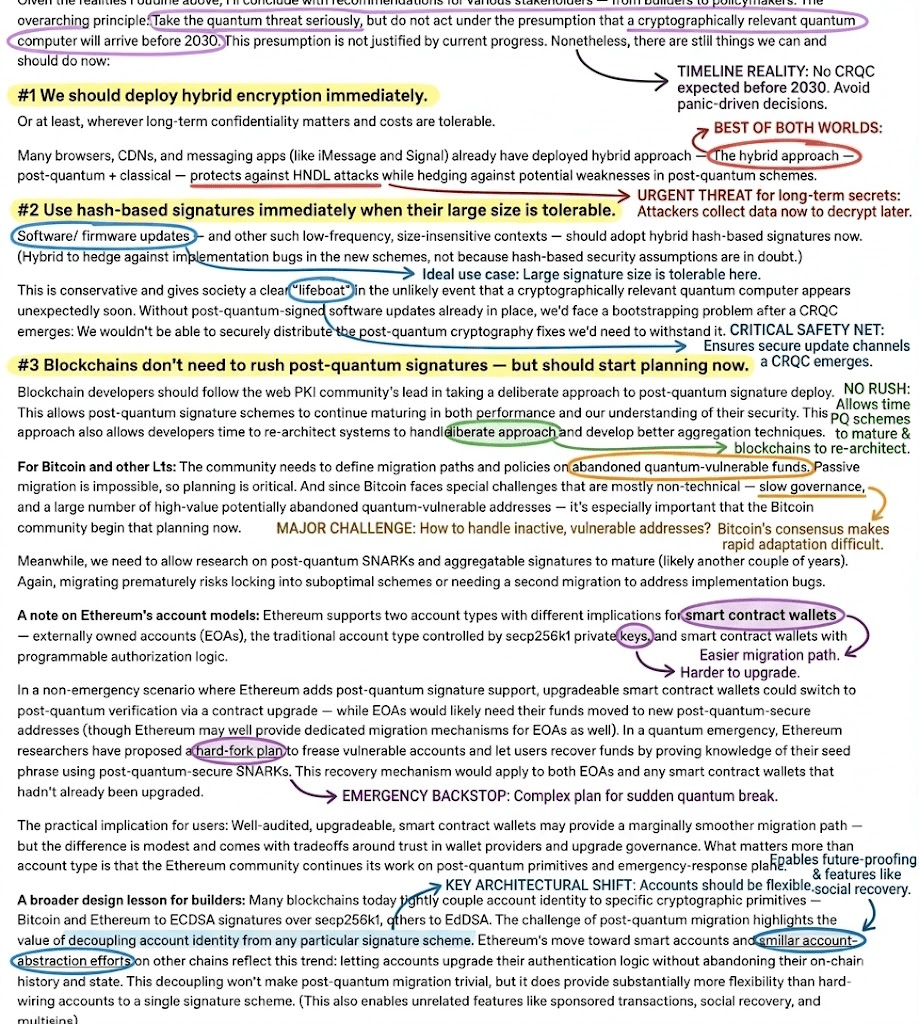
The correct strategy for blockchain entering the post-quantum era is not a panic-driven migration, but a structured advancement by domain and time scale: In the short term, scenarios involving long-term confidentiality (such as communication and update distribution) should immediately adopt a hybrid encryption of "classical + post-quantum" to resist HNDL attacks; in scenarios where volume overhead is tolerable, hash-based hybrid signatures should be deployed first to prepare "lifeboats" for potential future CRQC. However, blockchains should not hastily switch to post-quantum signatures because of their high performance cost, immature solutions, the ongoing development of aggregate signatures and SNARK systems, and premature deployment may lead to a secondary migration in the future. Currently, the most important thing is to plan the migration route, especially for L1 blockchains like Bitcoin, which need to clearly define strategies for handling abandoned addresses and vulnerable UTXOs; Ethereum and other smart account systems should continue to promote account abstraction, decoupling account identity from specific signature primitives to ensure future upgradeability. Privacy chains, facing the risk of HNDL deanonymization, should be migrated first or adopt a hybrid solution when performance allows. Meanwhile, the entire industry needs to focus more on implementation-level security in the coming years: vulnerabilities, side-channel attacks, and fault-based attacks are more realistic and urgent than quantum machines. Finally, society should continue to invest in quantum research and remain rational about media narratives of quantum breakthroughs, avoiding misinterpreting progress as a signal that "quantum is approaching the collapse of cryptography."
V. Summary
In 2025, quantum computing will not be a "black swan" that immediately destroys encryption systems, but rather a catalyst that drives the entire industry toward cryptographic modernization.