Dusk was founded in 2018 with a design point that most public networks still treat as an afterthought: regulated and privacy focused financial infrastructure is not a branding angle, it is a systems requirement. Dusk is a layer 1 that positions privacy and auditability by design as a default property of the ledger, not an overlay that an institution must bolt onto a transparent execution network. The detail that changes the story is that Dusk is aiming at the day to day mechanics of regulated markets, where confidentiality, record keeping, and supervisory access are all simultaneously mandatory, and where failing any one of them breaks the whole workflow.
To keep the analysis grounded, I will use a single organizing framework that is specific to Dusk’s mission, which I call the Permission Weave. In the Permission Weave, Dusk is evaluated by how tightly it braids three threads that regulated finance cannot separate: disclosure control that is enforceable in production, selective visibility that is usable across multiple counterparties, and verifiable confidentiality that can satisfy audit scope without publishing sensitive details. Each thread only matters if it produces an operational consequence, so throughout this piece the question is not whether Dusk can be private, it is whether Dusk can allocate visibility rights in a way that still yields clean settlement finality, durable data availability, and defensible governance.
What surprised me is that Dusk’s strongest positioning for regulated finance is not that it can hide information, it is that it can prevent over disclosure. In many institutional environments, full transparency is a liability because it forces firms to either avoid on chain settlement altogether or to replicate the entire process off chain to preserve confidentiality. Dusk’s compliance first financial infrastructure flips that constraint by making selective visibility a native path, so the default posture is not public exposure with exceptions, it is controlled disclosure with proofs. That is a contrarian point because most creators treat privacy as a retail preference, while the real institutional demand is privacy preserving compliance that reduces the blast radius of data exposure and the cost of maintaining parallel records.
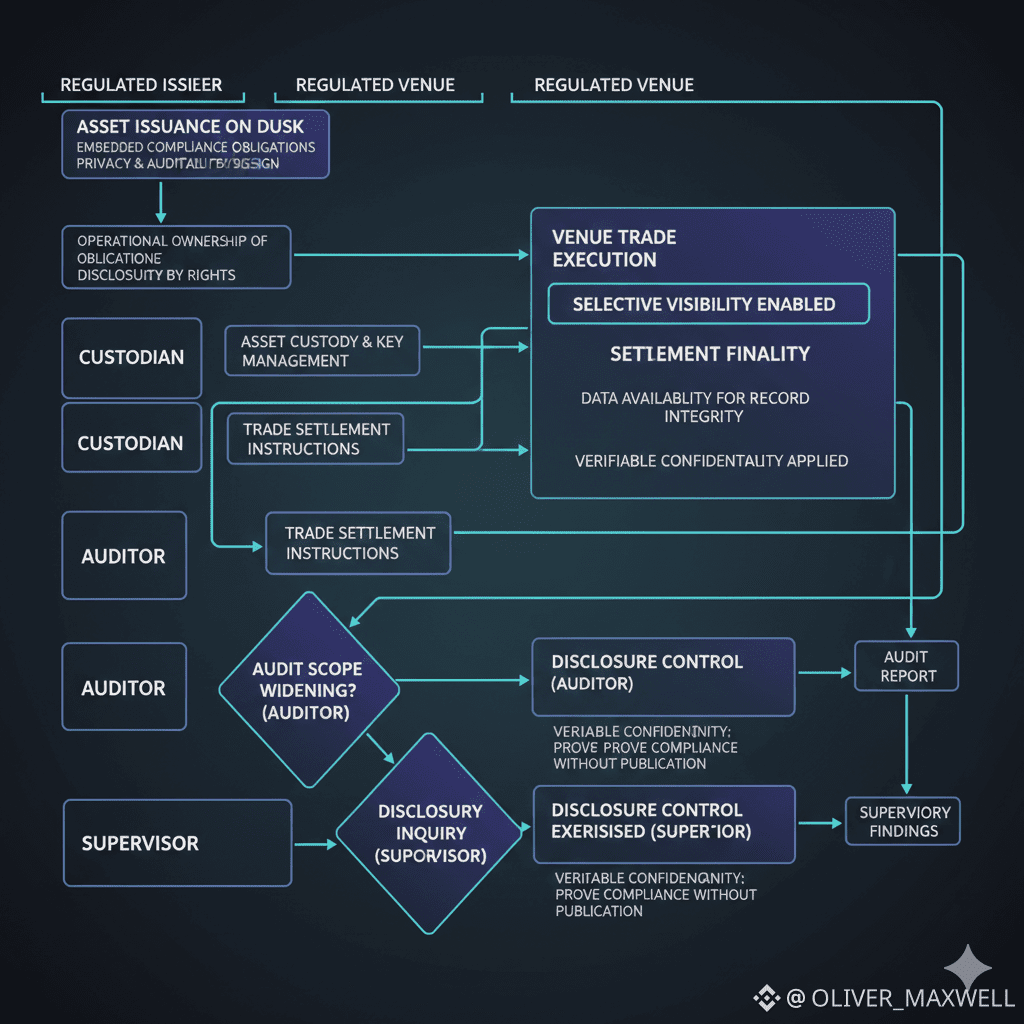
The Permission Weave starts at issuance, because tokenized real world assets are where compliance obligations are born and where auditability must be designed in, not appended later. A regulated issuer on Dusk needs a workflow where issuance terms, eligibility constraints, and ongoing obligations can exist alongside privacy and auditability by design. The operational consequence is that the issuer can structure disclosure rights so that sensitive cap table information, allocation logic, or investor attributes are not broadly visible, while still preserving a path for verifiable confidentiality when an auditor or supervisor later requests evidence. If Dusk cannot make that balance routine, then institutional grade applications do not scale beyond pilots.
Move one step forward to distribution and secondary activity, where a regulated venue and a custodian become the center of gravity. On Dusk, the venue needs selective visibility that supports trade execution without leaking counterparty intent, and it needs settlement finality that is legible to post trade operations, not just to protocol engineers. The custodian needs disclosure control that maps cleanly onto operational ownership of keys and permissions, because custody is not only about holding assets, it is about controlling who can see what and when. If Dusk’s privacy model forces either party to maintain shadow books to reconstruct events, the Permission Weave breaks and compliance first financial infrastructure becomes a slogan rather than an operational reality.
Now consider the audit and supervision path, where Dusk’s privacy and auditability mechanics must prove their worth under stress. An auditor does not want a narrative, the auditor wants an audit scope that can be bounded, replayed, and evidenced, and a supervisor wants targeted access that does not require requesting a full data dump. Dusk’s verifiable confidentiality should allow a firm to prove compliance within an inquiry window without widening visibility beyond what the inquiry requires. Data availability matters here in a very specific way: records must remain retrievable and consistent over time, even when most participants never had broad visibility in the first place. If Dusk cannot sustain that combination, institutions will treat it as an additional reconciliation burden rather than an infrastructure upgrade.
Dusk’s modular architecture is the second spine of the Permission Weave, because regulated adoption is as much about integration governance as it is about cryptography. Institutions rarely adopt monoliths without clear boundaries between execution environments, policy logic, and operational controls. With modular architecture, Dusk can support institutional grade applications that need predictable interfaces for compliant DeFi and tokenized real world assets, while keeping privacy and auditability by design as invariant properties. The operational consequence is that a regulated organization can assign ownership of different control domains, for example product, compliance, security, and operations, without turning every upgrade into a cross functional fire drill.
That said, two uncomfortable tradeoffs show up immediately when a serious institutional buyer evaluates Dusk. The first tradeoff is key management for disclosure rights, because disclosure control implies that access is mediated by keys, policies, and governance decisions, not informal trust. If disclosure keys are mishandled, an institution either cannot satisfy an audit request on time, or it discloses more than intended, and both outcomes are failures that trigger incident response. This is not theoretical, it becomes a standing operational obligation involving rotations, custody procedures, segregation of duties, and documented control testing, and it changes the staffing model required to run Dusk in production.
The second tradeoff is governance risk, specifically the governance decision surface that surrounds privacy and auditability by design. Regulated organizations build controls that assume certain disclosure semantics will remain stable over multi year audit cycles. If governance decisions can materially alter selective visibility behavior, validation rules, or disclosure control reliability, then Dusk becomes harder to qualify as durable compliance first financial infrastructure. The uncomfortable part is that institutions must treat governance not as community participation, but as a protocol change management risk that needs monitoring, internal approvals, and contingency planning, which can slow adoption even if the technology is sound.
This is where the DUSK token becomes structurally important without being promotional. DUSK token staking incentives can fund a long horizon security budget that supports validator responsibilities, and those responsibilities underpin settlement finality and data availability that auditors and supervisors ultimately rely on. In the Permission Weave, the DUSK token is not a growth story, it is the economic mechanism that can either stabilize or destabilize institutional readiness. If staking incentives are aligned, validators have a reason to behave predictably, keep execution environments reliable, and preserve the integrity of privacy and auditability paths. If incentives are misaligned, institutions will perceive Dusk as an operational dependency with unpredictable failure modes.
It is also worth stating what Dusk is not optimizing for, because that reveals why its design choices matter. Dusk is not competing to be a general purpose playground where everything is maximally transparent and composable at any cost. Dusk is oriented toward compliant DeFi, tokenized real world assets, and institutional grade applications where selective visibility is a feature, not a limitation. The operational consequence is that teams evaluating Dusk should measure it against their control frameworks, audit timelines, and supervisory expectations, rather than against retail centric narratives. When that lens is applied, privacy preserving compliance becomes the core capability, and the question becomes whether Dusk reduces net compliance friction relative to traditional stacks.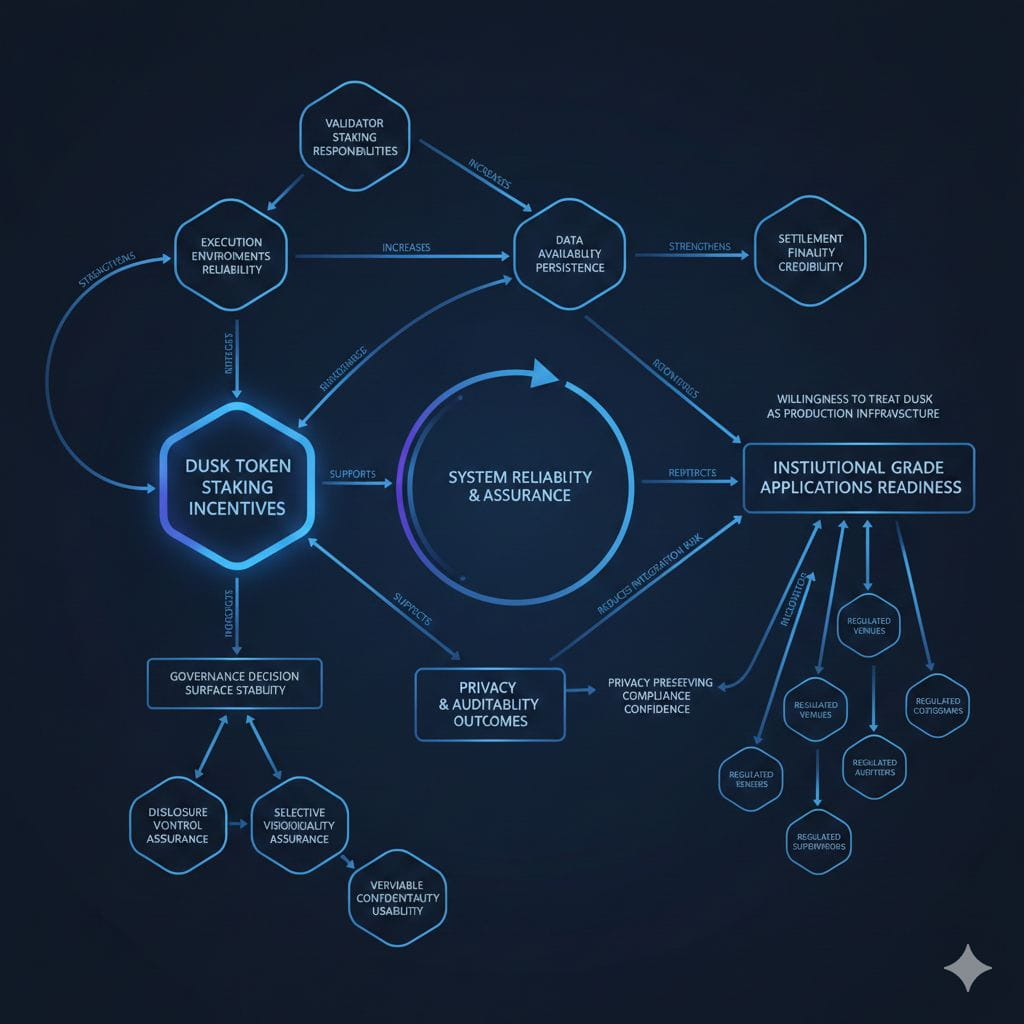
Internal memo style guidance for a regulated adopter of Dusk should read like control documentation, not marketing. Audit scope must define which Dusk events are in scope for each product, how verifiable confidentiality is used to evidence compliance, and how disclosure control is granted, revoked, and logged across the issuer, venue, custodian, auditor, and supervisor. Key management for disclosure rights must have named owners, rotation schedules, break glass procedures, and clear separation of duties, because disclosure keys are part of the control plane. Incident response must include scenarios where selective visibility fails open or fails closed, with playbooks for regulatory notification, forensic preservation supported by data availability, and internal reconciliation anchored to settlement finality. Integration risk must be owned explicitly across execution environments and modular architecture boundaries, with change management gates that track governance decision surface updates, validator responsibility assumptions, and the operational evidence a supervisor would expect during an inquiry window.
A conditional and testable prediction follows from the Permission Weave and from current pressure in regulated tokenization toward privacy preserving compliance. If regulated issuers increasingly require programmable disclosure rights that can satisfy both auditors and supervisors without broad publication, then Dusk’s adoption should show up first as repeatable issuance programs where the same disclosure control patterns are reused across multiple products and venues, rather than as isolated demonstrations. You can test this by watching whether Dusk is chosen for workflows where audit scope and supervisory inquiry windows are explicitly designed into the settlement process, and whether production operators treat Dusk’s governance decision surface as stable enough to write multi year control documentation against it. If those two conditions do not become true, Dusk may still be technically compelling, but it will be confined to environments where institutions can tolerate higher operational ownership.
The forward looking conclusion is that Dusk can win regulated market adoption only if the Permission Weave stays tight under real institutional constraints. Dusk must keep privacy and auditability by design predictable across upgrades, maintain selective visibility that reduces over disclosure without blocking legitimate oversight, and support settlement finality and data availability that auditors will accept as evidentiary. The DUSK token must continue to fund validator responsibilities through staking incentives that create a long horizon security budget, because institutions will not build critical workflows on top of fragile economics. If those operational truths hold, Dusk becomes a credible compliance first financial infrastructure for tokenized real world assets and compliant DeFi, not because it is louder, but because it makes regulated behavior cheaper to prove.
