After researching this project properly, I can say it stands on solid ground compared to many others. We read the documentation, we looked at how they explain their vision, and it becomes clear they are building with intention. I am not saying it is perfect, but from a professional point of view, it shows discipline. In my knowledge, that discipline is rare in this space, and it is usually the first sign that a team understands the long game.
While studying Dusk Network, one thing stood out almost immediately. They are not trying to impress with surface-level concepts or buzzwords. Their attention is directed toward the deep technical layers that many projects gloss over. Privacy isn’t treated as an add-on or a feature to bolt on later it’s considered a foundational requirement. That mindset becomes especially clear when you examine how they approach hashing within zero-knowledge systems.
I’ll be direct here. Traditional hash functions were never designed for zero-knowledge circuits. Names like SHA-256 are well known and reliable in conventional computing environments, but once you place them inside algebraic circuits, their limitations become obvious. They introduce heavy structures, complex constraints, and unnecessarily large proofs. From what I studied, this directly affects performance, cost, and usability. Many projects accept these inefficiencies and move forward anyway. Dusk chose not to.
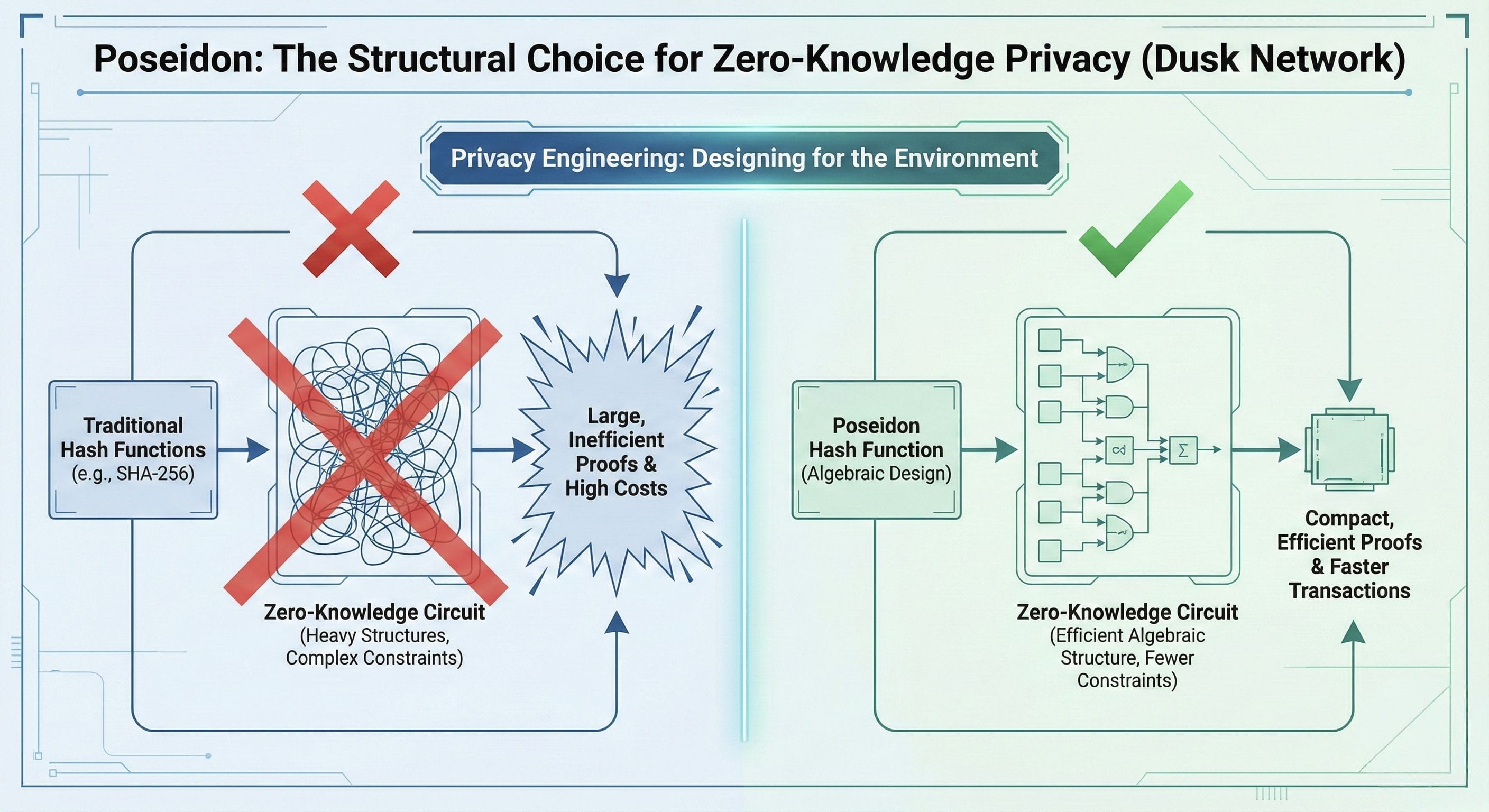
Instead, they adopted the Poseidon hash function, and from my research, this wasn’t a cosmetic decisionit was a strategic one. Poseidon is designed specifically to operate efficiently within arithmetic-based circuits. Its operations align naturally with the mathematical framework used in zero-knowledge proofs. When I looked into this design choice, it didn’t feel like a workaround. It felt like a solution built for the environment it actually runs in.
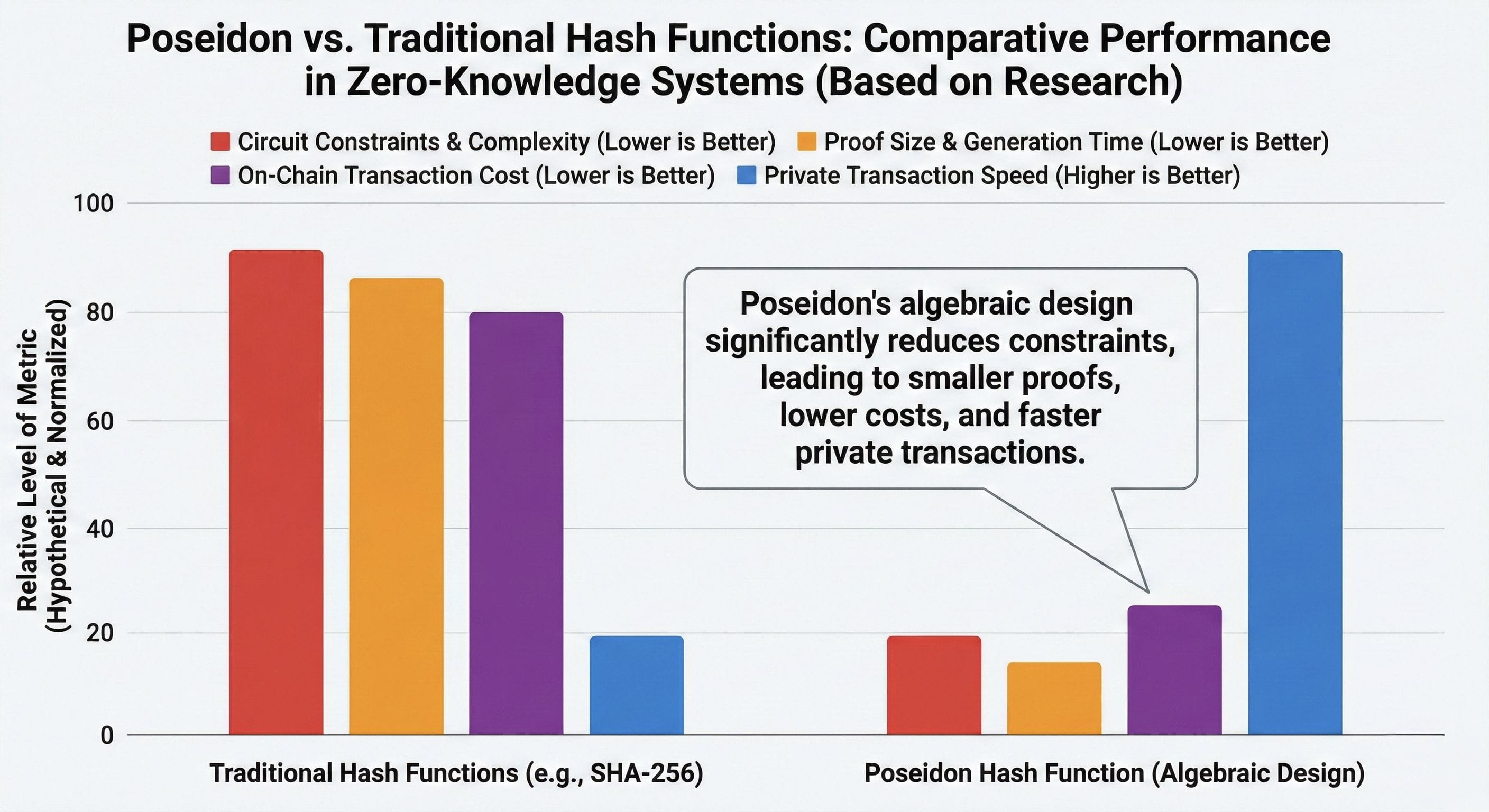
As you go deeper, the advantages become practical rather than theoretical. Poseidon significantly reduces the number of constraints required inside the circuit. In simple terms, proofs don’t grow unnecessarily large. I’ve seen privacy systems where proofs become so heavy that private computation turns into a luxury feature. Here, the opposite is true. Proofs remain compact, generation stays efficient, and verification remains manageable.
From a professional standpoint, this matters more than many people realize. Smaller proofs translate directly into faster private transactions. Faster transactions lead to lower costs when those proofs are processed on-chain. In my view, this is where many privacy-focused projects quietly fail. They work in theory but ignore the economic reality of blockchains. Dusk doesn’t. Performance and cost are treated as first-order design constraints, not afterthoughts.
What I personally appreciate is how this choice supports scalability without noise. There are no exaggerated claims here. Instead, the team improves the underlying mathematics so the system behaves better as usage increases. From my experience, reducing circuit complexity early prevents long-term bottlenecks. It keeps the system predictable and predictability is exactly what serious users and institutions look for.
Reliability is another subtle but important factor. Poseidon’s structure helps keep the proving process stable and consistent. From the explanations I reviewed, it’s clear the goal was a system that behaves the same under pressure as it does under ideal conditions. That kind of thinking usually comes from teams preparing for real-world adoption, not just attention.
From everything I’ve reviewed, Poseidon isn’t presented as a flashy selling point and that’s precisely why it matters. It quietly enables private computation to function smoothly without dragging the network down. It removes friction instead of masking it. In an ecosystem where many projects build impressive narratives on fragile foundations, this approach stands out.
Put simply, Poseidon is a key reason Dusk’s privacy model feels realistic. It keeps proofs lightweight, transactions efficient, and costs under control. I’m not here to oversell anything, but from a research-driven perspective, this is what careful engineering looks like: a real limitation identified and solved at the root. In my experience, that’s how strong systems are built.

