Walrus proposes time-locked blob primitives, which are automatically executed at specific blockchain epochs firing encrypted strategies, private keys or market signals in case certain predetermined conditions are met across global committees in Sui. Hedge funds commit large belief convictions in trade theses, i.e., specific entry levels of illiquid perp pairs, leverage levels of LP positions, coordinate of MEV search space, sealed until market structure changes establish thesis true. With funding spreads reversing either persistent or oracle spreads of more than 3bps, blobs decode via threshold quorums, providing alpha free of front-running risk or exposure to manual execution risk in volatile windows.
Concealment of Strategic Alpha.
Walrus time capsules incorporate DeFi strategies under verifiable delay functions tuned to the market cycles: 72-hour locks conceal the parameters of sandwich attacks until the mempool density decreases, 7-day locks conceal the parameters of rebalance trades until the volatility regimes concur on the point of reduced experience. Conditions on unlocks are verified with oracle consensus by multi-signature release committees, which consist of uncorrelated validators, before sliver reconstruction occurs, which blocks premature leaks that destroy edge. Chain slicing of provenance strategy is shown to be useful in construction of the theses in advance of market response, as well as safeguard intellectual property and perform performance verification by capital allocators.
Conditional execution layers go off on composite events: perp basis trades will be off when average of 7-day funding is over 0.15% AND implied vol surface 20% contango, MEV bundles will be off when block space auctions indicates miner capitulation. False trigger protection needs two affirmative notions, cutting through uncoordinated oracles, which slice early unlocks, burning our strategy capital. Two passages of the decisions are rebuilt to allow refinements to be discovered, the unfixed decision trees being created using post-execution analytics without revealing the existing positioning.
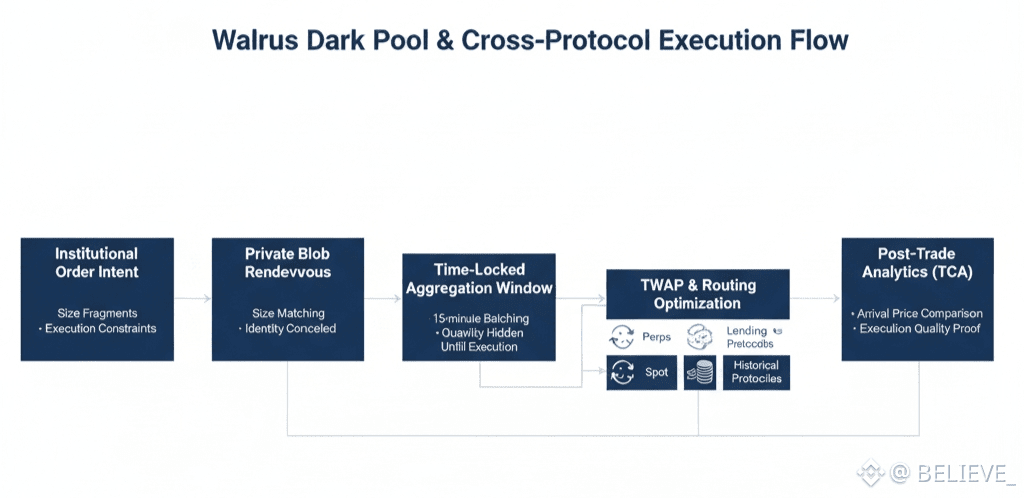
Dark Pool Liquidity Co-ordination.
Walrus coordinates institutional DeFi dark pools using privacy-preserving blob rendezvous-- big wallets groups match up size among fragmented venue orderbooks, with no information leakage. Aggregation contracts Time-locked aggregation contracts are aggregated on 15-minute windows, with matched quantities not disclosed until T +block height execution. Dutch auction clearing in the metadata of blobs present the optimum execution prices and hides the identity of participants by using zk-commitments.
Cross-protocol sweep executions are performed simultaneously in lending markets, in perps, and in spot venues which a large order is fragmented across, with time-locked routing algorithms which tradeoff slippage versus historical fill curves stored after previous sweeps. TWAP coordination among wallets of participants staggers market hanging with blob-synchronized randomness, and the execution quality is comparable to that of an OTC desk with on-chain transparency. The TCA automate Post-trade reports are based upon the tapes of the fill, uses benchmarking against arrival price deviations stored within the execution blobs.
Protocol Exploit Bounty Escrows.
Walrus bug bounty only disclose time-lock vulnerability reports under responsible reveal curves the payouts Member of the critical memory safety trigger pay 48-hour windows to fix protocols and then the proceeds to publicly disclose the vulnerability, Griefing attacks Member of the critical memory safety trigger pay 24-hour confirmations before the reactants can receive payouts. Refreeze Environment Exploit recreation environment uses vulnerable contracts, deployed in a remote, isolated blob sandboxes, allowing mainnet-safe whitehat verification and allowing full attack traces to be stored afterwards.
Calibration to economic security puts bounties out of protocol TVL exposure - smart contract reentrancy is the size of a bounty of 2.5 M, oracle manipulation is the size of a bounty of 10 M gradient scaled by the opportunities to manipulate. Staged payout waterfalls are based on partial discoveries which are rewarded with the static analysis warnings (10 percent) and a full award based on complete chains of exploits. Serial killer slashing imposes penalties on cross-blob tracked violation histories, and serial researchers gain skin in the game.
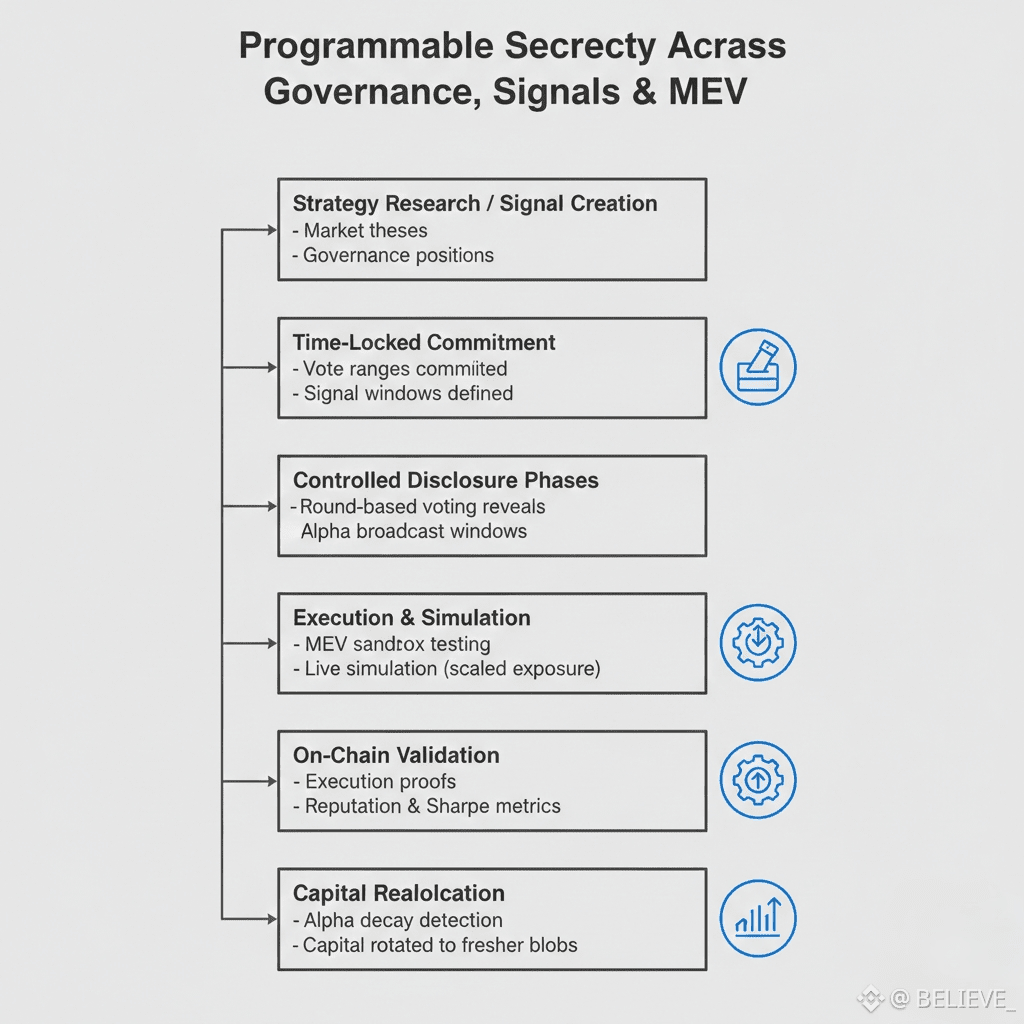
Coordination of Voting Strategy of the Institution.
Multi-round voting plans Walrus governance vaults keep secret progressive disclosure-based counter-strategies using a first-round preference leak, which do not reveal anything about a second-round counter-strategy, until the proposal has advanced. Whale coordination arises by the use of a commitment scheme that ties votes to published ranges but does not disclose the actual weightings of the scheme, does not allow the sale of votes but does allow signal boosting. Post vote implementation confirmation confirms executed ballots that have been done properly, and slashes the defectors waiting by their stakes.
Quadratic funding organizes small voter commitments in a form of effective bloc votes and time-locked reveal so that no one can gain undue Bloc vote power. Adversarial simulation of strategies simulates a series of game trees with the blobs anchored to historical outcomes of governance finding optimum voting equilibria prior to the lockup of proposals. Delegate portfolio optimization algorithms redistribute voting power within a cluster of issues, and optimize the alignment of protocols by tested preference elicitation.
Trading of Signals within the market.
Walrus alpha broadcast A broadcast channel measures exclusive access to research by time-bound blob windows, 24-hour windows on high-conviction catalysts, 7-day windows with quarterly thesis packages. The receiver blinding does not allow identification of the sellers and maintains the verification of delivery through threshold receipts. Dynamic pricing reacts to historical alpha decay curves, limiting distribution to below 2-sigma levels of signal strength.
Social trading websites replicate confirmed strategy execution by using position mirroring by blobs, and performance fees are charged based on Sharpe Hurdle velocity that is stored on execution history. Whisper networks introduce crowdsourced catalysts via anonymity-preserving aggregation surfacing regime shifts before introduced edges are diluted by disclosure. Signal provenance tracking is a reputation capital that aids in original researchers based on the attribution of their works, which is performed citation weighting, building reputation through the market cycles.
MEV Strategy Sandbox Testing.
The testing ecosystems Wives In the Walrus test environment, full state snapshots of EVM are used in blob-isolated sandboxes to execute backtests of bundle strategies on historical memorycoin pumps, stablecoin depegs, oracle attacks. Adversarial simulation introduces worst-case reorg sequences, flash loan attacks, sandwich defenses, to test cases, which are calibrated against test cases which are archived as blob-archived exploits. Gas optimization appears on a par with the same strategy application, with MEV capture enhancement emerging as execution trace diffs.
Live simulation Live simulation fills the gap between testnet execution and mainnet deployment by conducting 10% position size sizing in the first week, then 10 percentage point increases until full allocation has been passed on at the conclusion of 30 days of profit factor validation. Mutation engines of strategy are adapted to change of market regimes, and alpha is maintained by parametric evolution across changes in overall market regimes, without human recalibration.
Capital Efficiency Amplification.
Walrus leverage coordination systems coordinate margin-based gains across correlated trades, risking in capacity to capture yields in temporary window of opportunity opportunities without liquidation cascades risk. Dynamic collateral mobilization transfers unutilized balances in stablecoins into a short lending period in events of convergence of the basis, and, to maintain principal protection, automated unwind withdraws the principle. Cross-protocol yield optimization routes overcapitalize arbitrage loops that are identified by blobs and arbitrage on ephemeral spreads before the saturation of competitive saturation happens.
Performance bond contracts ensure limits to drawdown of strategies by third-party verification against published risk parameters so that capital allocators can use programs without manager due diligence. Alpha monitors cause automatic switching of capital to fresher blob strategies in response to alpha decay, with portfolio risk budget maintained by re-optimization.
Information asymmetry to the benefit of programs Programmable secrecy Walrus time-locked infrastructure uses the information asymmetry of DeFi to its advantage. The tactical disguise holds position. Dark pools are efficient in execution. Bounties align incentives. Voice is enhanced by voting coordination. Signal markets trademarks intuition. MEV sandboxes remove risk of deployment. Return compounds are due to capital efficiency. Institutions have impregnable safes where the advantage of the market lasts longer and longer the faster, and transient visions make lasting riches in all periods of change of the world with its epochs, all changes of the market order.



