What changes the story around Walrus is not that it offers decentralized storage, but that it treats storage as a set of enforceable operational promises rather than a vague pool of spare disk space. I will call this the Verified Blob Commitment Model. The model frames Walrus as a system that makes explicit commitments about data survivability, access control, and operator behavior, then wires those commitments directly into mechanics and incentives through WAL. The detail that matters is that these commitments are not social assurances. They are encoded in how data is split, distributed, paid for, retrieved, and governed on Sui. That framing is useful because it explains why Walrus feels less like a marketplace for storage and more like a programmable data layer for applications that cannot tolerate silent failure or arbitrary censorship.
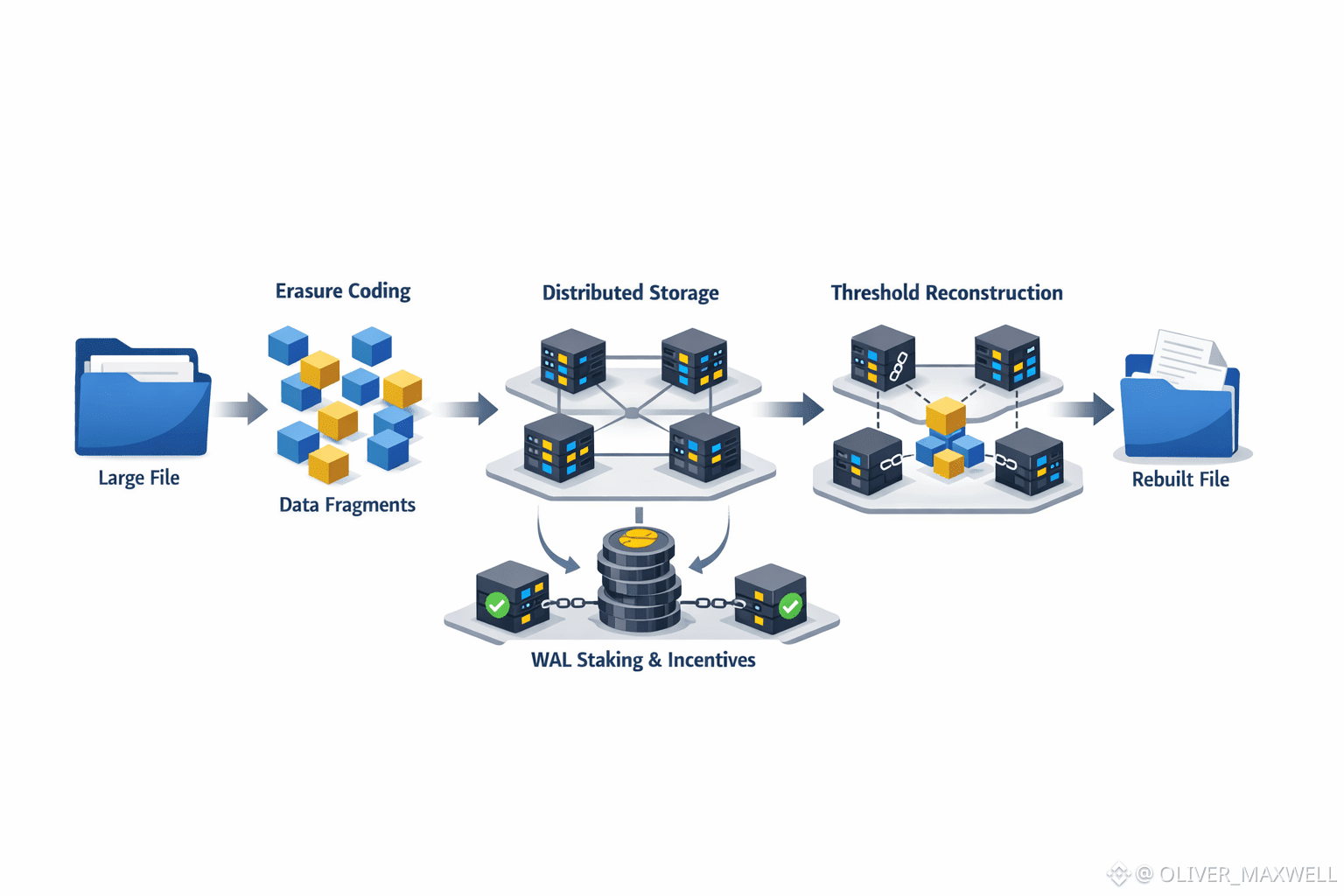
A typical Walrus workflow begins with an upload that is immediately transformed before it ever becomes a liability to a single node. Large files are broken into blobs and passed through erasure coding, which produces multiple fragments with mathematically defined redundancy. This is not naive replication where every node holds a full copy. Instead, any sufficient subset of fragments can reconstruct the original data. Those fragments are distributed across a decentralized set of storage operators coordinated through Sui. Payment and resource commitments are expressed onchain, binding storage obligations to WAL-based incentives. The practical result is that durability is not a promise of eternal uptime from any one machine, but a probabilistic guarantee that reconstruction remains possible even when nodes churn, go offline, or are selectively unavailable.
Retrieval under churn is where the erasure coding choice reveals its economic logic. Because Walrus only needs a threshold of fragments rather than all replicas, retrieval tolerates partial failure by design. This gives Walrus a clear cost advantage over older decentralized storage models that rely on full replication everywhere. The cost driver shifts from raw duplication to fragment availability, which is cheaper to maintain at scale. Censorship resistance at the data layer follows naturally. No single operator can suppress access by withholding a complete file because no operator holds one. The network only fails to serve data if a large enough subset of independent operators collude or disappear simultaneously, which raises the bar from administrative pressure to systemic collapse.
Private interactions add another layer that is often misunderstood. Walrus does not treat privacy as an offchain habit where users hope nodes behave. Access control is part of the storage interaction itself. Data can be stored in a way that enforces who can reconstruct it and under what conditions, using onchain rules on Sui to coordinate permissions. For dApps, this means private transactions and selective disclosure become properties of the data layer rather than application level patches. The tooling around Walrus supports this by letting applications define how blobs are accessed, who can retrieve them, and how those permissions evolve over time through governance.
The role of WAL is easiest to understand when viewed as behavior shaping rather than speculation. Staking ties operator rewards to reliability, making uptime and honest participation economically rational. Governance gives WAL holders a policy surface to adjust parameters that affect redundancy thresholds, incentives, and acceptable risk. This matters because erasure coded systems always involve tradeoffs between cost and resilience. By anchoring those choices in WAL governed rules, Walrus avoids hardcoding assumptions that will age poorly as workloads change. Cost efficiency emerges not from underpaying operators, but from aligning payment with the minimum redundancy required to meet explicit durability guarantees.
There is a contrarian insight here that most decentralized storage discussions miss. Privacy and decentralization often increase cost, not reduce it, because they eliminate economies of scale enjoyed by centralized cloud providers. What surprised me when analyzing Walrus is that erasure coding combined with blob distribution can reverse part of that equation. By reducing full replication while preserving failure tolerance, Walrus can apply privacy controls without multiplying storage costs linearly. On Sui, where data heavy onchain applications are becoming more common, this matters right now. The constraint is no longer transaction throughput alone, but the ability to store and retrieve large volumes of application state without reverting to centralized infrastructure.
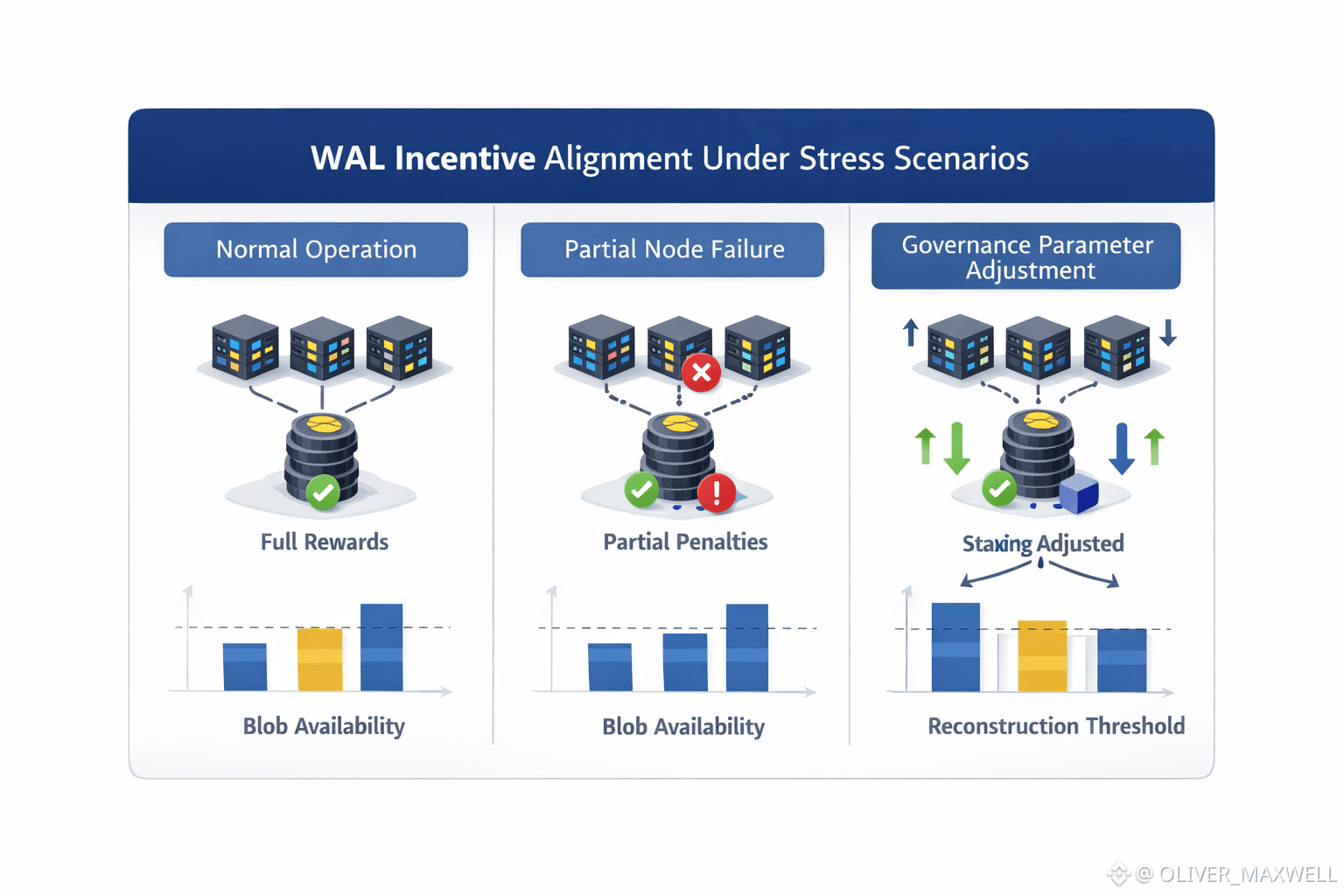
Two uncomfortable tradeoffs deserve attention. The first is operational latency. Erasure coding and fragment coordination introduce overhead during upload and reconstruction. For applications that require instant access to large blobs, this can be a real constraint. Walrus mitigates it through threshold based retrieval, but it does not eliminate it. Builders must decide whether durability and censorship resistance justify slightly more complex data flows. The second tradeoff is incentive precision. WAL staking aligns behavior, but it also concentrates governance influence among participants willing to lock capital. Poorly tuned incentives could favor cost minimization over resilience if governance decisions drift. This is not a flaw unique to Walrus, but erasure coded systems amplify the consequences of miscalibration because redundancy levels are explicit levers.
From an institutional perspective, the evaluation looks different. An internal memo would focus on audit scope and control surfaces rather than ideology. Walrus offers clear advantages in avoiding vendor lock in because data fragments are distributed and reconstructable without dependence on a single provider. Key management for access control becomes central, as private interactions rely on correct permissioning rather than perimeter security. Compliance teams will ask how incident response works when data availability degrades and what durability guarantees can be contractually inferred from erasure coding thresholds. Integration risk sits at the intersection of Sui based coordination and existing data pipelines. Walrus’s strength here is that its guarantees are mechanical and inspectable, not marketing claims, but enterprises will still demand rigorous internal validation.
Looking forward, a testable prediction is that Walrus adoption will correlate with the rise of onchain applications whose data footprint grows faster than their transaction count. If application builders continue to push richer media, complex state, and private interactions onchain, the pressure to decouple data availability from centralized clouds will intensify. Walrus will benefit if it can keep tuning WAL governed parameters to balance cost and resilience under that load. Its constraint will be governance agility. Slow or fragmented decision making around redundancy and incentives would show up quickly as either rising costs or degraded availability.
